Encryption Keys
migVisor uses the same keys for all customers except the metadata scanned by the collector, where the customer can choose to use dedicated keys for encryption.
Encryption Methods
Encryption at Transit
migVisor Collector:
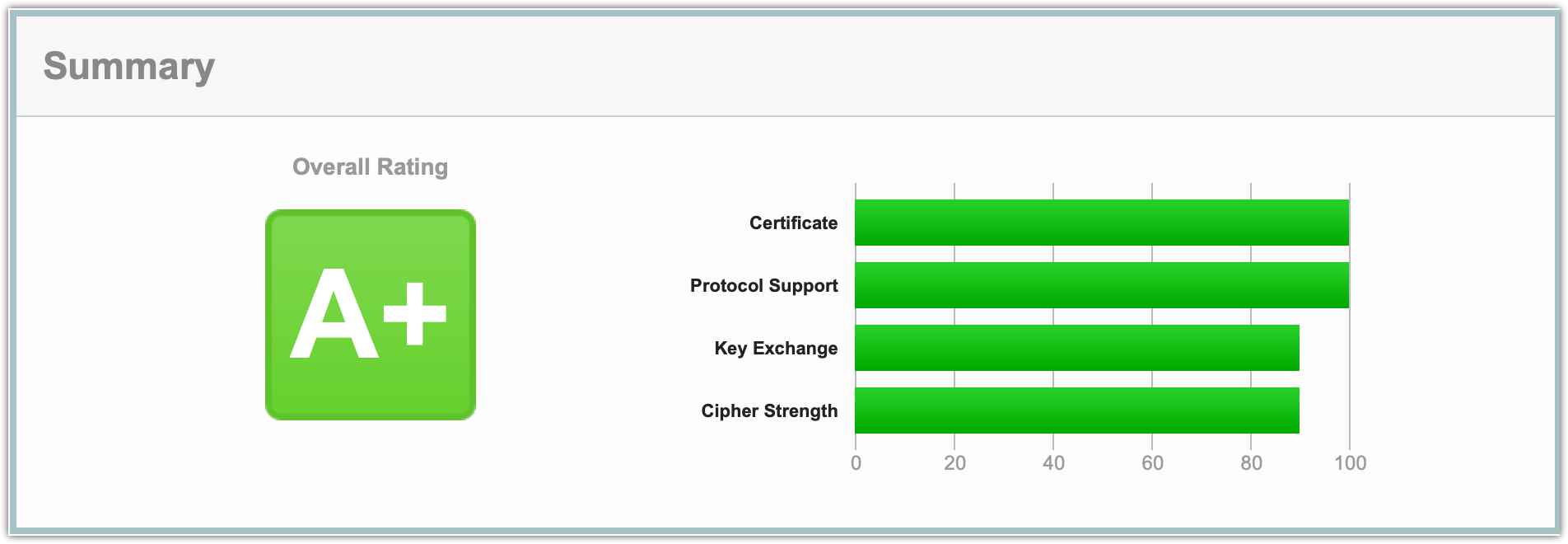
migVisor Console:
For all properly configured RDBMS engines supported by migVisor, a secure connection will be used. If TLS is required, the JDBC driver will attempt to use it which may require a manual wallet or keystore. If the server is configured to accept TLS connections, it will be used. However, the driver does not currently check the certificate's validity.
To ensure that the connection is encrypted, the server can be configured to enforce accepting secured connections, and if enforced from the databases server side, data encryption during transit via the Oracle Native Network Encryption is maintained.
Encryption at Rest
To secure data at rest during the data collection, migVisor provides a mechanism to randomly generate a unique encryption key which can then be used to encrypt the data collected using mMC for data in transit and data at rest in all stages prior to the point where the data reaches migVisor’s infrastructure.
AWS
In migVisor, encryption at rest is configured and integrated with KMS.
The data encryption is done using the Advanced Encryption Standard (AES) algorithm, AES-256:
All uploaded files are stored in an SSE-S3 encrypted bucket.
All data, logs, backups, and snapshots of Amazon RDS are encrypted within AWS managed symmetric key stored in KMS.
All tables of Amazon DynamoDB are encrypted using AWS owned symmetric key.
Internal application credentials are placed encrypted in helm charts. Once deployed, the credentials are placed as application-layer secrets in EKS and encrypted with a customer managed symmetric key stored in KMS.
For more information, see https://docs.aws.amazon.com/whitepapers/latest/logical-separation/encrypting-data-at-rest-and--in-transit.html.
Azure
All data that is stored by Microsoft is encrypted at the storage layer using the Advanced Encryption Standard (AES) algorithm, AES-256.
Internal application credentials are placed encrypted in helm charts. Once deployed, the credentials are placed as application-layer secrets in AKS and encrypted with a customer managed symmetric key stored in Azure Key Vault.
For more information, see https://learn.microsoft.com/en-us/azure/security/fundamentals/encryption-atrest.
GCP
The data encryption is done using the Advanced Encryption Standard (AES) algorithm, AES-256:
All uploaded files are stored and encrypted with SSE in Cloud Storage.
All data, logs, backups, and snapshots of Cloud SQL are encrypted within GCP managed symmetric key.
All information in Cloud Firestore is encrypted with SSE using GCP managed symmetric key stored.
Internal application credentials are placed encrypted in helm charts. Once deployed, the credentials are placed as application-layer secrets in GKE and encrypted with a customer managed symmetric key stored in KMS.
For more information, see Default encryption at rest | Documentation | Google Cloud.
Encryption Key Management
The key retention policy follows the cloud vendor and EPAM retention policies.
Access to the cryptographic keys is restricted to authorized users and services using Identity and Access Management (IAM).
Key management and all data access operations are captured in audit logs and include identity information, such as user details, time signature, API operation, etc.
AWS
migVisor uses Amazon-managed envelope encryption, where a data key is used to encrypt data and is itself encrypted under a KMS key stored in AWS KMS. The key encryption is done strictly within FIPS 140-2 Security Level 3 boundary.
Azure
migVisor uses Microsoft-managed data encryption keys and Azure Key Vault as a key management service. The key encryption is done strictly within FIPS 140-2 Security Level 2 and Security Level 3 boundary.
GCP
migVisor uses Google-managed data encryption keys and Google Cloud KMS as a key management service. The key encryption is done strictly within FIPS 140-2 Security Level 3 boundary.